- The flaws could enable attackers to take control over a currency’s entire blockchain transactions and conduct fraudulent operations.
- The research team claims that the two issues were discovered in August 2018.
Two extremely dangerous security flaws have been discovered in 26 Proof-of-Stake (PoS) cryptocurrencies. The flaws dubbed as ‘Fake Stake’ attacks can allow an attacker to crash rival network nodes and gain remote access of the same up to 51 percent.
Side-effects of the flaws
The flaws were discovered by a group of four academics from the University of Illinois at Urbana-Champaign in the US. The researchers found that the flaws could enable attackers to take control over a currency’s entire blockchain transactions and conduct fraudulent operations.
PoS cryptocurrencies are particularly based on chain-based PoSv3 (Proof-of-Stake version 3). They draw the basic codes from Bitcoin’s codebase, with the PoS functionality grafted in them. However, some of these design codes are copied inappropriately, thus leading to new vulnerabilities.
“We call the vulnerabilities we found ‘Fake Stake’ attacks. Essentially, they work because PoSv3 implementations do not adequately validate network data before committing precious resources (disk and RAM). The consequence is that an attacker without much stake (in some cases none at all) can cause a victim node to crash by filling up its disk or RAM with bogus data. We believe that all currencies based on the UTXO and longest chain Proof-of-Stake model are vulnerable to these “Fake Stake” attacks,” the researchers wrote on Medium.
Impacted cryptocurrencies
The research team claims that the two issues were discovered in August 2018. Upon discovery, it started contacting the development teams of the affected cryptocurrencies in October.
However, some of the development teams could not be informed as their GitHub accounts appear to have become inactive. Demo code for reproducing the two vulnerabilities is available on GitHub.
The list of impacted cryptocurrencies includes the names of NavCOIN, Qtum, Emercoin, HTMLCOIN, ReddCoin, CloakCoin, BitBay, Linda, Phore, PotCoin and more.
Although some cryptocurrencies have deployed mitigations for the reported bugs, researchers believe that these mitigation processes are not fool-proof. Hence, they are looking out for better ways to address the problem.
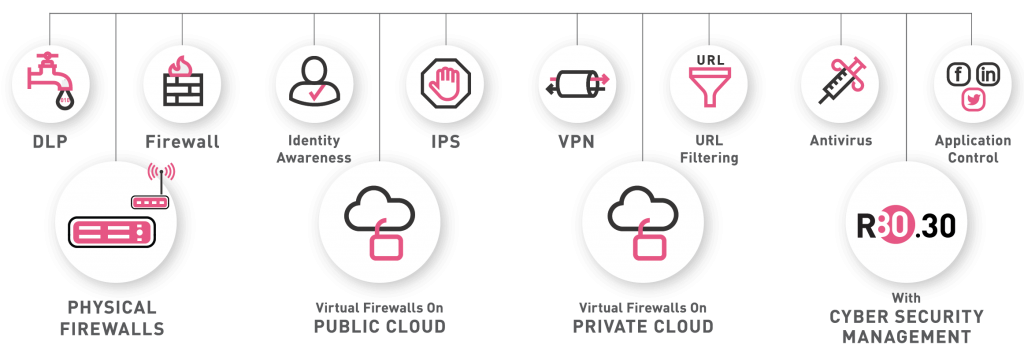
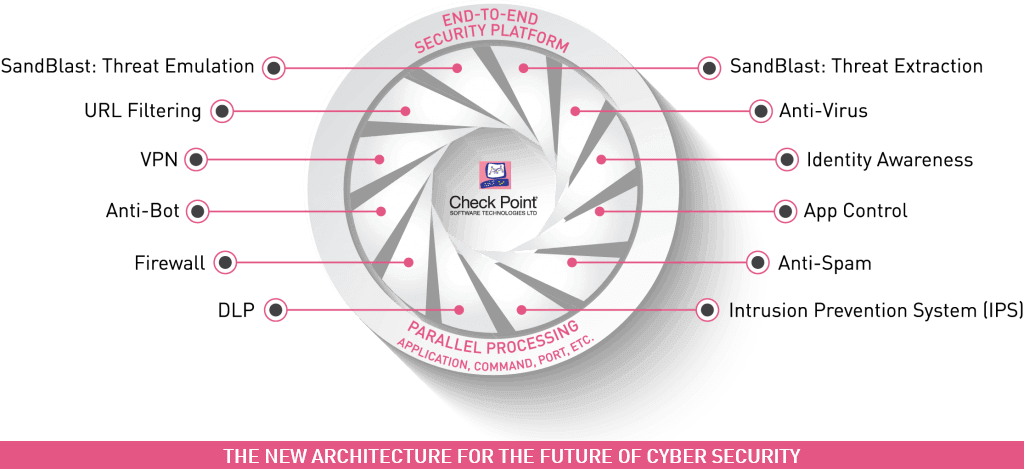
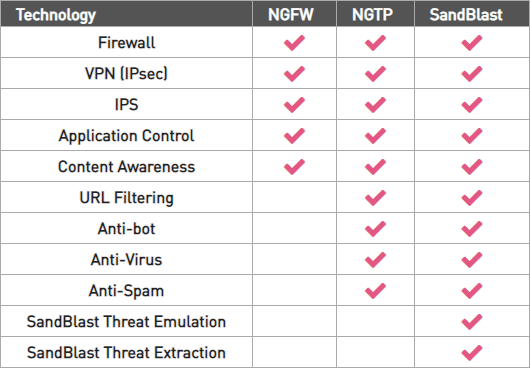
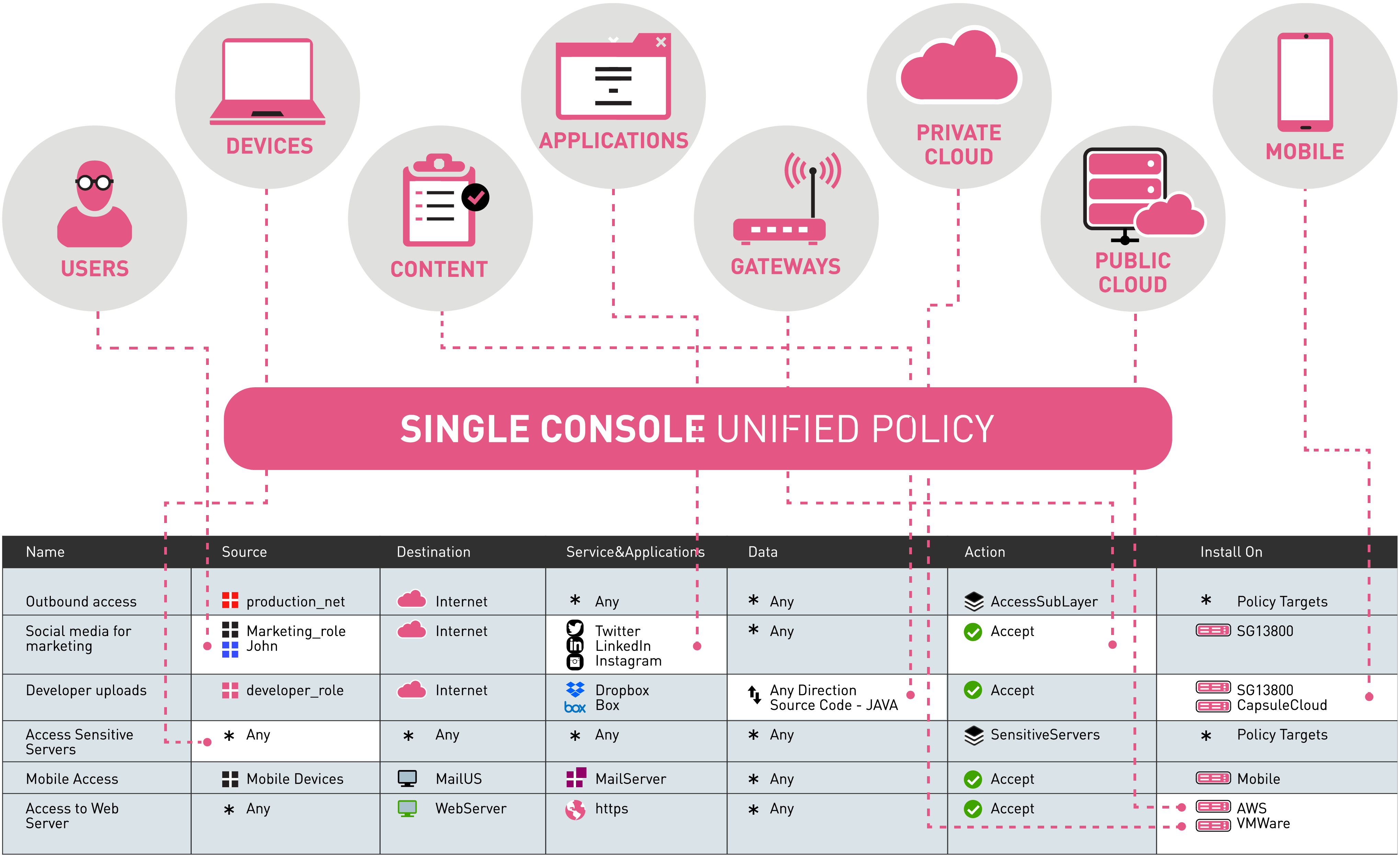
 Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Cyber Security Company in India Provides Next-Generation Firewalls for advanced protection for physical,virtual public,private cloud networks
Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Cyber Security Company in India Provides Next-Generation Firewalls for advanced protection for physical,virtual public,private cloud networks