How can we avoid\prevent a ransomware attack
Since last few years ransomware has evolved into one of the biggest threats to cyber security, the number of cases reported each day is growing exponentially. These attacks are spread across globe. As a proactive measure, we are hereby notifying our clients on the measures required to enhance security posture towards securing web sites and web servers.
What is ransomware?
Ransomware is a malware that stealthily gets installed in your PC or mobile device and holds your files or operating system functions for ransom. It restricts you from using your PC or mobile device, and from accessing your files (files are sometimes locked or encrypted), unless you pay the ransom (in exchange for file decryption).
Paying the ransom (either through credit card or Bitcoins) however, does not guarantee that you’ll get your files back. Prevention is still way better than allowing yourself to be infected and then trying to find a cure.
What does a ransomware attack look like?
Ransomware targets your pictures, documents, files, and data that are personally invaluable.
You can tell that you are under attack when you see any of the following:
- Ransomware note
- Encrypted files
- Renamed files
- Locked browser
- Locked screen
Files on the computer will be encrypted with unknown format and it will be unrecognizable:
When can a ransomware attack start?
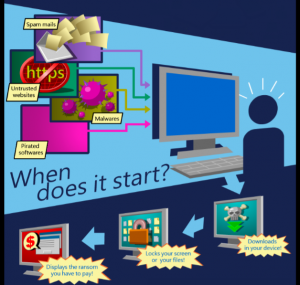
Potential victims can fall into the ransomware trap if they are:
- Browsing untrusted websites
- Not careful about downloading or opening file attachments which are known to contain malicious code from spam emails. That also includes compressed files or files inside archives. Some possible attachments can be:
- Executables (.ade, .adp, .ani, .bas, .bat, .chm, .cmd, .com, .cpl, .crt, .hlp, .ht, .hta, .inf, .ins, .isp, .job, .js, .jse, .lnk, .mda, .mdb, .mde, .mdz, .msc, .msi, .msp, .mst, .pcd, .reg, .scr, .sct, .shs, .url, .vb, .vbe, .vbs, .wsc, .wsf, .wsh, .exe, .pif, etc.)
- Office files that support macros (.doc, .xls, .docm, .xlsm, .pptm, etc.)
- Installing pirated software, outdated software programs or operating systems
- Using a PC that is connected to an already infected network
How can we avoid\prevent a ransomware attack :
- Do not keep password which is easy to crack. Please do not use “password” variants in the password. Ex : P@ssw0rd12, Pass1234. change to complex, kindly use http://passwordsgenerator.net/
- Implement IP based access lists on firewall rules in Cloud, restrict use of configuration allowing server access from “Any” in source.
- Keep backups of your files, either by copying the files to an offline location or by availing Veritas NetBackup/Commvault Backup services from NxtGen.
- Replication services with 24 hours checkpoint can help you restore the server to the state prevailed before the attack was executed
- Keep your operating system, antivirus, and installed software patches up to date.
- Avoid suspicious websites, emails, and files online, which might hide Trojans which can get downloaded to your computer
- Disable remote access from unknown sources, Restrict RDP access from ANY . IT should be immediately changed to access from specific IP on specific port only.
- Avoid running Macros on the server
- In some cases, brute force attack is employed to gain access to the system, where the default user accounts are tried for different passwords using password cracking software’s.
- Disable the default user accounts ex : guest, admin, administrator . Keep user names which are difficult to guess.
- Please provide admin access to user accounts only if necessary, if a user with admin access downloads a malware from infected website, it might infect all the systems connected in a local network
- Enable user account lockout if multiple attempts are made to login to the server.
- Employ SSL certificate to access website and by defining authorized browsers to be used to access the websites.
- Selectively allow few necessary firewall ports. Block all unwanted ports.
- Please do not allow hacker to discover your server by scanning on essentials ports. If you are allowing DNS, AD, database ports to be accessed through the public network, your server is more prone to these attacks.
- Restrict user accounts based on the role
- There is very little chance of decrypting the files since these ransomware uses High end encryption.
Few references:
https://blogs.technet.microsoft.com/mmpc/2016/05/18/the-5ws-and-1h-of-ransomware/
https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx
http://www.computerweekly.com/feature/How-to-avoid-being-caught-out-by-ransomware
 Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Cyber Security Company in India Provides Next-Generation Firewalls for advanced protection for physical,virtual public,private cloud networks
Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Cyber Security Company in India Provides Next-Generation Firewalls for advanced protection for physical,virtual public,private cloud networks