Network Security Audit Company in India
Network Security Audit Company in India
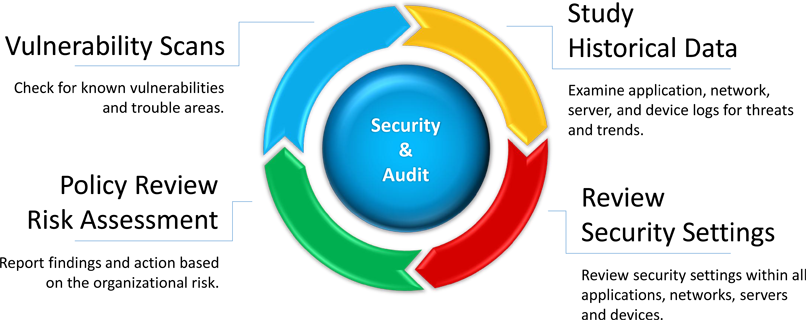
Firewall Firm offers security audit services. These audits include applications, Operating systems, Networks and policy. Details of these audit processes are as below:
Policy Audit
Policy Audit service are deals with auditing of security policies. With our experience in dealing with various diverse systems and policies, we offer a unique combination of audit as well as technology skills. Policy Audits helps clients to recognizes their weaknesses and strengths as formulated in their policies and take adequate measures to reach standards prevalent elsewhere in this area.
Application Security
Firewall Firm looks into applications and audits existing policies on applications keeping in view the objectives of the client organization in terms of security. We also help clients develop secure and state of art applications through our solutions which are indicated elsewhere on this site.
Operating System Security
Operating system is the backbone which provides the platform on which applications are hosted. Firewall Firm has extensive experience in plugging the known vulnerabilities and hardening the operating system for client use. Audit services also help the client in understanding the weaknesses which exist in the system.
Network Security
Network security audit service audits the security of the network. This service looks into the areas of confidentiality, authentication and data integrity. Firewall Firm solutions team is capable of building these features on any network using standard protocols. Firewall Firm also helps clients in proper selection of network security appliances like Firewalls, IDS’s, Antivirus software and PKI solutions.
Vulnerability Assessments Services in India
Vulnerability Assessments are essential to find out the extent to which systems are exposed to threats from internal as well as external users. Firewall Firm provides these tests using the best of breed tools. You can request a sample report of the Vulnerability Assessment here. Firewall Firm conducts Vulnerability Assessment Tests in the following two ways:
Onsite Vulnerability Assessment Tests
Onsite Vulnerability Assessment is done by deploying Firewall Firm’s assessors to the client’s locations. These assessments include:
Assessment of vulnerabilities on Operating Systems ( only for servers on public IP addresses) verifying if the recent patches are applied or not.
Automated vulnerability assessments of routers and Firewalls.
Assessing the vulnerabilities on web servers, RAS, mailservers which are accessible from outside.
A detailed report regarding vulnerabilities found with recommendations for plugging the same.
Remote Vulnerability Assessment Tests
Remote Vulnerability Assessment is done by remotely accessing the Client Servers which are kept on public IP addresses. These tests include:
Assessment of vulnerabilities on Operating Systems ( only for servers on public IP addresses) verifying if the recent patches are applied or not.
Automated vulnerability assessments of routers and Firewalls.
Assessing the vulnerabilities on web servers, RAS, mailservers which are accessible from outside.
A detailed report regarding vulnerabilities found with recommendations for plugging the same.

Cyber-Security-Audit-Review
For more details, please contact us on
 Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Cyber Security Company in India Provides Next-Generation Firewalls for advanced protection for physical,virtual public,private cloud networks
Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Managed Cyber Security Company in India Firewall Firm is a Cyber Security Company in India Provides Next-Generation Firewalls for advanced protection for physical,virtual public,private cloud networks